Today, the Woo engineering team deployed a critical update for WooCommerce that fixes a vulnerability that could allow bad actors to inject malicious content into your browser. The Woo team is also reaching out to WooCommerce merchants whose stores may be vulnerable.
This issue was only occurring on WooCommerce stores. Next WooCommerce Version That too Order attributes are valid, Features enabled by default in WooCommerce:
| 8.8.0 | 8.8.1 | 8.8.2 | 8.8.3 |
| 8.8.4 | 8.9.0 | 8.9.1 | 8.9.2 |
If you’re running WooCommerce 8.8.0 or higher, we strongly encourage you to update as soon as possible.
Actions you can take to keep your store up to date
If you don’t already have the correct version installed, Manual update.
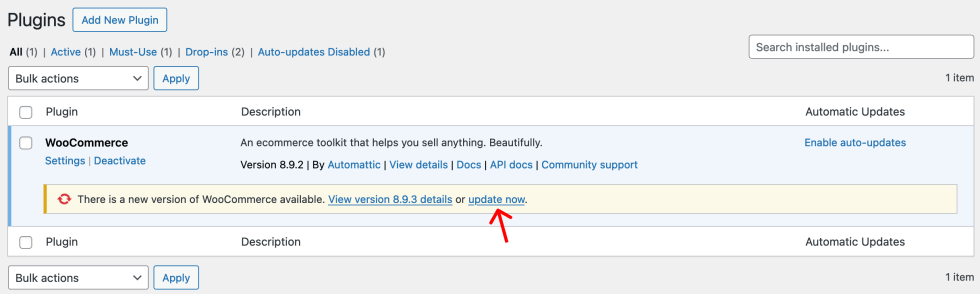
To update an extension:
- Log in to your store’s WP admin dashboard, Plugin.
- Location WooCommerce In the list of installed plugins and extensions, you will see a warning like this: “A new version of WooCommerce is now available.”
- click Update now The link provided in this alert will take you to the latest version 8.9.3.
If you can’t update WooCommerce right away, you should Disable order attributionThis vulnerability is only exploitable if Order Attribution is enabled.
For more information about the update, please click here. Woo Developer AdvisoryLearn how to check your store’s version status and more.
What is a vulnerability?
This vulnerability allows: Cross-site scriptingis a type of attack where a bad actor manipulates links to include malicious content (via JavaScript or other code) on a page, potentially affecting anyone who clicks on the link, including customers, merchants, and store administrators.
Has my store’s data been compromised?
We have not received any reports of this vulnerability being exploited in the wild. This issue was originally discovered through a proactive security research program jointly run by Automattic and HackerOne. Our support team has not received any reports of this vulnerability being exploited in the wild, and our engineering team’s analysis has not received any reports of this vulnerability being exploited in the wild.
I’m using a version of WooCommerce older than 8.8.0, is my store affected?
The vulnerability affects WooCommerce stores running WooCommerce 8.8.0, 8.8.1, 8.8.2, 8.8.3, 8.8.4, 8.9.0, 8.9.1, and 8.9.2. In particular, stores that run Order Attributes Enabled (This is enabled by default.) If you’re using a previous stable update version of WooCommerce, your store will not be affected.
How do I know if my store is safe?
Your store The latest patched version of WooCommerce (8.9.3)safe.
What else can you do to keep your store safe?
We always encourage our merchants to maintain high security standards, which includes using strong passwords, two-factor authentication, carefully monitoring transactions, and using the latest, secure versions of WooCommerce (and any other extensions or plugins installed on your site). Read more about security best practices.
If you have any further concerns or queries, our team of Happiness Engineers are here to help. Open a support ticket.
Special Thanks
We thank security researchers for their help EcalonFor helping discover this vulnerability as part of Automattic’s research. HackerOne Bounty Program.






